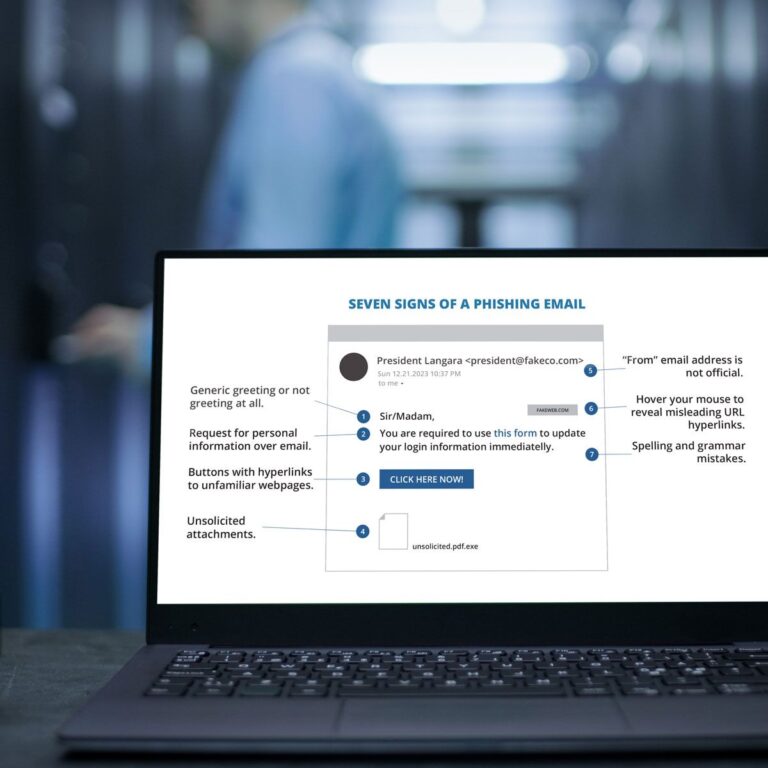
Phishing emails are a common tactic used by cybercriminals to steal sensitive information from unsuspecting victims. This is also one way that your business and all the data within it can be hijacked if the right measures aren’t taken and implemented across your whole team.
Phishing emails are designed to look like legitimate communications from trusted sources, such as banks, government agencies, or well-known companies, and often contain urgent language or requests for sensitive information.
But how can you spot a phishing email, and what should you do if you receive one? In this blog post, we’ll take a closer look at the anatomy of a phishing email and provide steps to take for each component.
The first thing to check when you receive an email is the sender’s address. Phishing emails often come from fake or impersonated addresses that look similar to legitimate ones.
For example, instead of “support@yourbank.com,” a phishing email might come from “support@yourbank.co” or “support@yourbank-support.com.”
If you’re not sure whether the sender is legitimate, it’s important to do some research. Look up the sender’s name and email address online to see if they match up with the legitimate organization. You can also contact the organization directly to verify the legitimacy of the email.
Phishing emails often use urgent language or make promises of a reward to entice recipients to open the email. Common subject lines include “Your account has been compromised” or “You’ve won a prize!”
If the subject line seems too good to be true or creates a sense of urgency, it’s important to be cautious. Hover over the subject line to see if the email address is legitimate, and be wary of opening any attachments or clicking on any links.
The body of a phishing email often contains language designed to create a sense of urgency or fear. For example, the email might claim that your account has been compromised and that you need to log in to fix the issue. The email might also contain a link that takes you to a fake login page that looks like the real one.
It’s important to be cautious when clicking on links in emails. Always hover over the link to see if it’s legitimate before clicking on it. If you’re not sure whether the link is legitimate, don’t click on it. Instead, go directly to the organization’s website and log in from there.
Phishing emails often request sensitive information such as usernames, passwords, or credit card details. These requests might come in the form of direct questions, such as “What is your password?” or “Can you confirm your credit card details?”
It’s important to never give out sensitive information in an email. Legitimate organizations will never ask for sensitive information in an email. If you receive an email asking for sensitive information, delete it immediately and report it to the organization.
If you receive a phishing email, the first thing to do is to not panic. Remember that cybercriminals are trying to create a sense of urgency or fear to get you to act quickly. Take a deep breath and follow these steps:
The best way to protect yourself from phishing emails is to use caution when opening and engaging with emails. Don’t wait for a phishing email to strike.
Contact JEI Tech today to schedule a consultation and learn how we can help you protect your business from cyber threats.
Take Our Cyber Security Quiz
How does your cyber security posture stack up? Take our short quiz to see!
Providing IT Support, Consulting, Service and partnership in: High River, The Foothills, Nanton, Okotoks, Calgary, Grand Prairie, Fort Macleod, Lethbridge & Southern Alberta
Copyright 2017 – 2024 Jolee Electronics Inc. t/a JEI Tech| Beautifully Crafted by Freshly Pressed | All Rights Reserved | Terms & Conditions | Privacy Policy